Connected cars have a large cybersecurity risk surface
As cars become digitally connected to each other and the road infrastructure, their cybersecurity risks are multiplying
‘Connected cars’ promise efficiency and safety gains, including fewer traffic collisions and road fatalities. They also carry significant cybersecurity vulnerabilities, which are often overlooked: either because security upgrades seem prohibitively costly or because of a culture of denial within the automotive industry where traditional manufacturers have little experience tackling cybercrime.
What next
As connected cars become ubiquitous, the opportunity and incentive for cybercriminals to target them will increase. Some attacks will narrowly target individuals (for financial or geostrategic gain), but there is a growing risk of fleet-wide attacks since a vulnerability in a particular make and model will likely extend to all vehicles in that range.
Subsidiary Impacts
- Continuing consolidation and cross-country partnerships within the auto sector will extend IT vulnerabilities to multiple manufacturers.
- Connected cars will generate vast amounts of data; ensuring the safety and privacy of these will challenge auto firms.
- Cybersecurity opens another major risk frontier for auto manufacturers already struggling with changing emissions rules.
Analysis
A connected car is simply a car with internet access. Features typically include smartphone interfaces, so people can connect their phones to stream music or find nearby restaurants, as well as the ability to turn the car into a wifi hotspot. Such cars often have on-board navigators and roadside assistance systems.
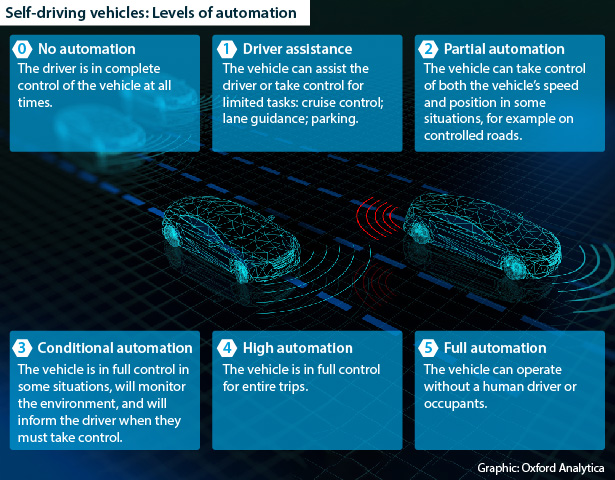
Driverless cars are the most advanced end of connected cars that make use of technologies such as GPS and radar to sense the environment around them so they can operate without a human driver or occupant.
Multiple risks
Connected cars have multiple cybersecurity risks (see PROSPECTS 2019: Cybersecurity - November 23, 2018).
CAN bus
All modern cars have a controller area network (CAN) bus that acts as a central point which enables communication between the electronic control units -- small computers that control almost every system such as brakes and steering.
This makes the CAN bus a central point of vulnerability. Even more concerning, the CAN bus is insecure by design. First developed in 1983 when cybersecurity was not a major concern, it lacks basic security features such as authentication and encryption. A systems upgrade is considered too costly by auto manufacturers.
Infotainment systems
Since multiple parts of a connected car have some form of wireless connectivity, nearly any of them can provide an entry route to a hacker to the CAN bus.
One route is the infotainment system, which typically has wifi or cellular connectivity. In 2015, a team of researchers hacked Fiat-Chrysler's Jeep Cherokee by exploiting a vulnerability in a proprietary platform that controls the car's infotainment system.
The vulnerability allows anyone who can obtain a car's internet protocol address (which can be 'brute forced' within an hour) to access the platform. Once the hacker has gained entry, they can implant malicious code to send commands through the CAN bus to the engine, wheels and other physical components.
The researchers were able to control the breaks and fully to shut down the engine at lower speeds, and to take control of the car remotely over the internet irrespective of distance, without any need for physical access.
They were later able to expand the attack to other Jeeps and other Chrysler cars (including Dodges) that use the same proprietary platform.
Telematics systems
Telematics systems, which provide monitoring and safety features, tend to make use of cellular or Bluetooth connections.
For example, in roadside assistance systems, which have cellular connectivity, researchers have found a vulnerability which allows them to gain access if they call the system multiple times.
Another route is hands-free calling systems, which pair a user's phone to the vehicle via Bluetooth: if a hacker infects that phone through a phishing attack, the malware could then make its way into the vehicle.
Software risks
Mobile applications that enable vehicle owners to interact with their connected cars are another vector. In 2016, researchers showed how they could hack Tesla's official app to steal a car.
Digital keys for cars are a similar entry point, as are software updates. Hackers could insert malware into an update, infecting the vehicle.
USBs and charging cables
Most connected cars have USB ports. An infected phone plugged into a car would transfer the malware.
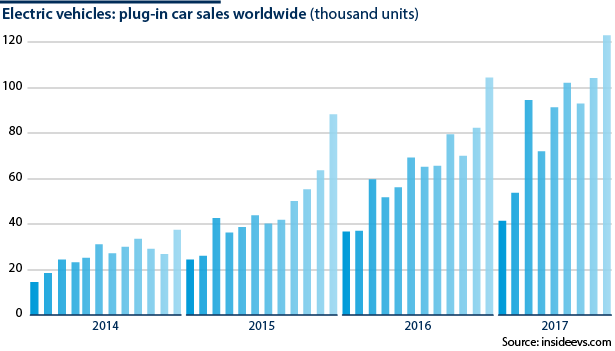
Electric vehicles, the market for which is expanding rapidly, are particularly vulnerable: if the charging cable infrastructure is infected with malware, all cars plugged in to charge would be affected.
V2V and V2I communications
Vehicle-to-vehicle (V2V) communication allows surrounding cars to communicate with each other over wireless networks to exchange information such as their speed and position. Vehicle-to-infrastructure (V2I) communications enable cars to communicate with highway infrastructure such as cameras, streetlights and lane markers.
If a hacker gains access to V2V or V2I communications, they could feed false information into the network, falsifying a car's position data and causing a crash -- or they could introduce malware onto the vehicle, and infect all cars connected to the network.
Such risks would be particularly acute for driverless cars, which must be connected via V2V and V2I technologies to operate effectively, and are powered by artificial intelligence systems that are vulnerable to digital manipulation.
Coding errors
At present, a connected car carries of over 100 million lines of code, which is more than in an F-35 fighter jet. The sheer size of the code means there are likely to be many bugs. In code of any type, the computing industry estimates, there are 15-50 errors per every 1,000 lines.
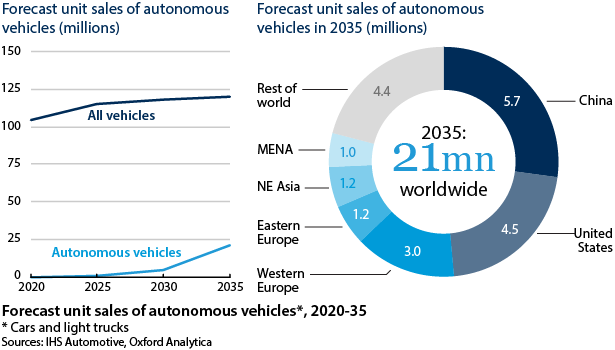
Automated vehicles are estimated routinely to have 200-300 million lines of code. With multiple suppliers providing parts of the code, the risk of writing and interoperability errors will rise further (see CHINA: Self-driving car plans will make rapid progress - July 31, 2018).
Industry response
Auto manufacturers such as Tesla, Fiat Chrysler and General Motors are increasing their investment in cybersecurity for connected cars.
Several industry consortiums have also been created to address this risk: in the United States, 14 automakers and two industry groups -- Auto Alliance and Global Automakers -- established an Automotive Information Sharing and Analysis Center in 2015 for the sharing best practice and cyberthreat information.
However, overall cybersecurity risks are proliferating faster than safety protocols.
Regulatory attempts
Regulatory regimes for the cybersecurity of connected cars are nascent
Governments have only started taking cognisance:
- In 2016, the US National Highway Traffic Safety Administration issued its non-binding Cybersecurity Best Practices for Modern Vehicles, which it followed up in 2017 with a guidance document specifically on automated driving.
- The EU Agency for Network and Information Security released a guidance document in 2017 entitled 'Cybersecurity and Resilience of Smart Cars'.
- In 2017, the UK Department for Transport issued a guidance document for self-driving cars specifically.
Outlook
Ransomware attacks will likely rise
Thus far, most cybercrime targeted at connected vehicles has been to steal the vehicle; this trend will likely increase.
Meanwhile, new risks will materialise.
Given the success of ransomware attacks on critical infrastructure in recent years, hackers are likely to target connected cars with similar malicious code, primarily for financial gain. (For example, the owner could be locked in or out of the car until they pay a ransom).
Cybercrime involving fatalities is a distinct possibility. Skilled hackers, especially those linked to nation-states or organised crime, might target particular individuals, for example by tampering with braking systems using electronic means.
Other attacks involving fatalities would most likely be carried out by terrorists or other adversaries, potentially by using a driverless vehicle as a weapon. Vehicles have already been used in multiple terrorist attacks.