Prospects for cybersecurity in 2022
The pandemic has created new and intense cybersecurity risks for companies and governments
The COVID-19 pandemic has intensified multiple cybersecurity issues that are likely to be salient in 2022 and beyond. Organisations face increased pressure to provide security for remote workers, prevent phishing and ransomware attacks, and deploy new technologies such as artificial intelligence (AI) systems safely. Meanwhile, geopolitical tensions in cyberspace have also intensified, particularly since the damaging cyberattacks against prominent US targets by Russian and Chinese state actors and criminal hackers.
What next
The adoption of zero trust network architecture (ZTNA) will expand next year, particularly among large organisations operating critical infrastructure amid rising US government pressure. Official pressure will be less effective in containing online misinformation, not only about COVID-19 vaccines but also climate change. Ransomware attacks against healthcare entities and critical infrastructure are a major risk, but cross-country law enforcement coordination will also intensify.
Strategic summary
- Increasing adoption of AI tools across sectors poses new cybersecurity challenges.
- Geopolitical tensions in cyberspace will intensify in 2022, especially in relation to Chinese cyber activity and influence on the international internet infrastructure.
- The US government will rally its foreign partners to undertake coordinated action against ransomware groups linked to Russia.
- Policy and regulatory solutions will lag despite the rising social and political harm of online misinformation.
Analysis
The COVID-19 pandemic has exacerbated multiple cybersecurity issues.
Remote work
Many workers are unlikely to return to full-time onsite working post-pandemic and will permanently adopt hybrid working patterns. The shift to remote work has accelerated the adoption of advanced security measures such as multi-factor authentication and of ZTNA.
According to a July 2021 Microsoft report, in a cross-sector survey of 1,200 security decisionmakers across the United States, Germany, Japan, Australia and New Zealand, 76% of the respondents reported implementing ZTNA, with 35% of them nearing full implementation.
Remote and hybrid working patterns will require new security upgrades
ZTNA adoption will rise next year, particularly in the United States where the government has issued an executive order requiring its adoption at federal agencies and strongly encouraging private critical infrastructure firms to do the same. However, smaller organisations will find the cost and complexity of ZTNA prohibitive (see INT: Adoption of zero trust cybersecurity will be slow - July 5, 2021).
Large-scale remote working has also underlined the benefits of migrating data and workflow to cloud platforms. This has increased customer focus on the security and resilience of cloud services; efforts on both fronts will advance next year (see INTERNATIONAL: Resilience of cloud services will rise - November 15, 2021).
Social engineering
Social engineering attacks, such as COVID-themed phishing emails, have increased during the pandemic.
According to a UK government report in March 2020, phishing attacks were the most common threat vector in the country, with 83% of businesses and 79% of charities reporting experiencing such an attack over the previous twelve months. Yet organisational preparedness has a long way to go: of the 1,410 businesses and 487 charities surveyed, only 52% and 47%, respectively, reported mock phishing training exercises.
The need for upgrading defences will intensify as such social engineering attacks become more sophisticated with the criminal use of deep and cheap fake technology for image and voice cloning.
Ransomware
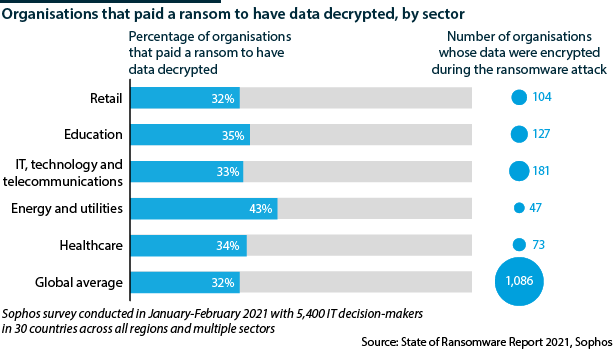
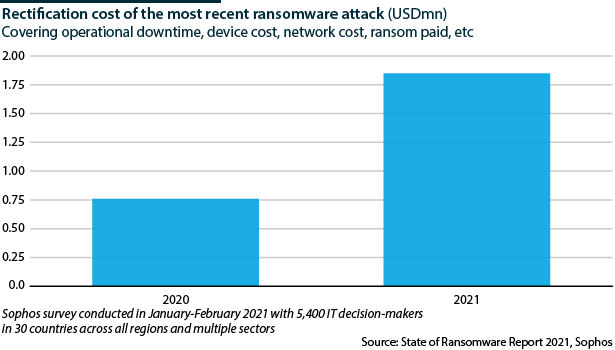
Ransomware has also emerged as a prominent threat, with the cost of remediating such an attack rising substantially and 32% of organisations paying the ransoms.
The May 2021 ransomware attack against the US energy company Colonial Pipeline highlighted the risk and cost of this type of cyberattack for critical infrastructure (see INT: Infrastructure sees rising cybersecurity risk - May 18, 2021). The threat of ransomware will remain serious in 2022 due to the strong financial incentives for cybercriminals to engage in such attacks.
Ransomware can be delivered by a number of vectors, including via phishing attacks requiring an element of social engineering and via vulnerabilities in external-facing services such as Windows Remote Desktop Protocol that can be exploited without manipulating a human user. Therefore, effective defences will require broad cybersecurity resilience policies that combine user awareness and technical security tools (see INT: Efforts to curb ransomware crimes face limits - June 14, 2021).
Meanwhile, law enforcement action against ransomware gangs will rise next year, building on the success of actions in 2021 against ransomware groups DarkSide and REvil (see INT: REvil hackers' fate will deter cyber criminals - November 9, 2021). Cross-country cooperation will intensify, spurred by the White House's new, informal 30-member Counter-Ransomware Initiative, and ongoing talks between the United States and Russia over Russia-based ransomware gangs.
Attacking AI
Cybersecurity of AI applications is likely to acquire increased significance in 2022, partly as the use of such applications proliferates across sectors. The Mitre Corporation, which has developed a matrix of threats to AI applications to complement its threat matrix for non-AI systems, expects that 30% of cyberattacks in 2022 will be targeted at AI applications.
Cyberattacks on AI tools will rise
Yet legislative tools to ensure the security of AI applications will lag in all major markets, except the EU and the United Kingdom. The EU Artificial Intelligence Act is expected to come into force next year, and there are moves towards similar legislation in the United Kingdom.
Online misinformation
Another cybersecurity issue exacerbated by the COVID-19 pandemic is the spread of online misinformation, which lowered public compliance with social distancing rules, and, more damagingly, public trust in vaccination.
While misinformation is spread by a variety of actors for different reasons, some has been orchestrated by state-linked actors, specifically Russia and China. Disinformation campaigns orchestrated by the Russian state to undermine confidence in COVID-19 vaccines developed in Western countries continued throughout 2021 and are likely to continue into 2022.
Misinformation about climate change could also intensify next year. A November 2021 civil society report said that climate misinformation is viewed up to 1.36 million times daily on Facebook, and that user engagement with such posts (in the form of reactions, comments and shares per post) has increased 76.7% since the start of 2021.
Yet most governments will lack the policy tools to make social media and other online forums more accountable for user-posted contented. The UK government and the EU are likely to be the notably exceptions; their online content regulation bills are expected to be enacted next year (see UK: Online Safety Bill faces tough legislative road - October 21, 2021 and see INT: Rules on social media misuse lag despite harms - August 4, 2021).
Geopolitical tensions in cyberspace
Geostrategic rivalry in cyberspace is likely to intensify in 2022, with Chinese activity in cyberspace receiving as much if not greater scrutiny than Russian actions. This is the result of a wider deterioration in China's ties with the West and China's role in the 2021 Microsoft Exchange attack (see CHINA: Cyber tools will be deployed carefully - September 16, 2021 and see US/CHINA: Microsoft hack will widen rifts on cyber - March 24, 2021).
Beyond state-linked attacks and misinformation, Western democracies are increasingly concerned about China's influence over the global internet infrastructure. Beijing's proposals to increase centralised control of the internet directly, such as by implementation the 'New Internet Protocol' developed by Chinese company Huawei, are unlikely to be accepted by liberal democracies. However, China will use its increasing economic and political influence to shift international norms on internet governance indirectly towards greater state control and in ways that advantage Chinese technology vendors. This ambition has been firmed up in China's October 2021 guidelines on technical standardisation (see CHINA: Beijing's profile will rise in standard-setting - October 27, 2021).
Resilience
Although cyberthreats are evolving in terms of frequency and sophistication, cybersecurity resilience will also rise.
One indication during 2021 of increasing levels of cybersecurity resilience was the successful prevention of disruption to the Tokyo Olympics by cyberattacks, despite warnings of high levels of risk prior to the event, and reports of millions of attempted attacks during the event itself.
The success demonstrates the value of:
- proactive threat management (for example, in conducting attack simulation exercises);
- international cooperation (Japan cooperated with the US government and other partners); and
- public-private cooperation (between domestic and foreign IT companies).
This approach to cyber defence provides a model for future high-profile events.